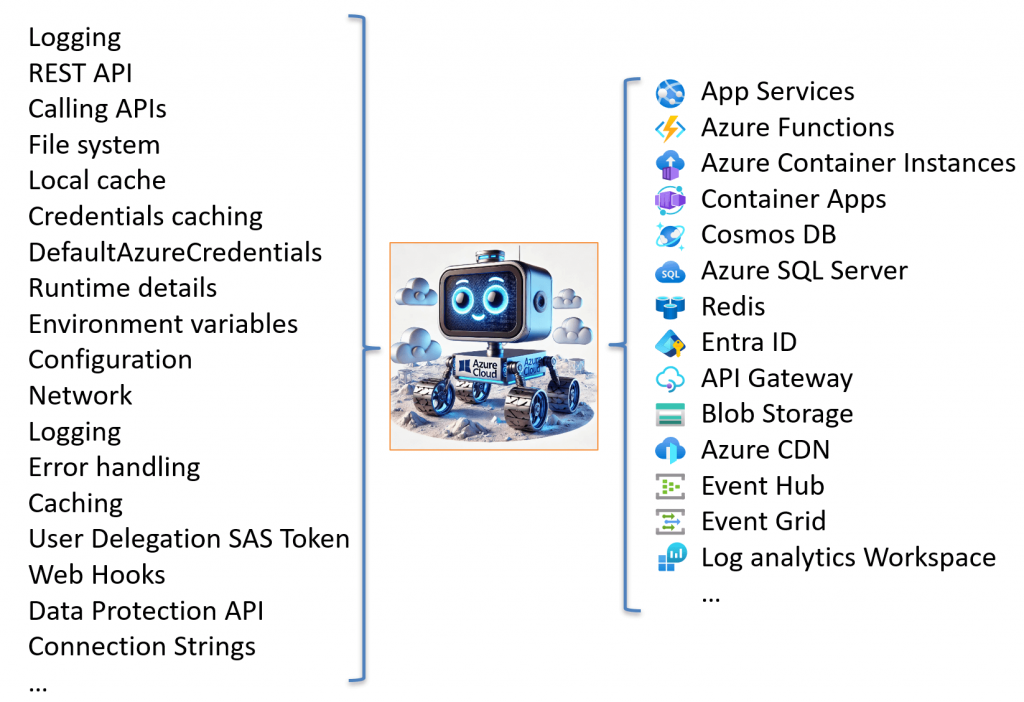
The Cloud Debugger is an open-source tool for Azure developers to explore, learn, and troubleshoot their Azure cloud environments. Whether preparing for Azure certification, looking to streamline debugging, or aiming to deepen your understanding of Azure, Cloud Debugger provides the tools to make the cloud more discoverable.
Background – Getting Azure certified
As I prepared for the AZ-204 Azure developer certification, I realized that I needed to build something larger to understand the Azure Cloud and the services covered by the Azure Developer certification. Just doing the included exercises was not enough. This led to me creating this open-source tool designed to help learn and simplify the debugging process for Azure applications.
The Mars Rover vs. Azure Analogy
When we explore Mars, we send rovers to measure, observe, and perform experiments to understand the unknown.
Developers also need a systematic approach when navigating Azure’s vast and complex cloud environment. Cloud Debugger is designed to provide this by enabling you to explore, experiment, and gain deeper insights into your cloud setup.
Cloud Debugger as a Teaching Tool for Azure
A secondary purpose of this tool is to serve as an exercise platform for future Azure training. Rather than relying solely on theoretical exercises, Cloud Debugger offers a hands-on environment where developers can actively engage with Azure services, troubleshoot real-world scenarios, and experiment with different configurations, features, and concepts.
What can the Cloud Debugger for Azure do?
The Cloud Debugger offers over 30 specialized tools to help developers explore, diagnose, and understand their Azure environment. These tools include:
HTTP Request tools
- Current request viewer
View details about the current request.
- Request Logger
Provides a list of all the received requests. - Calling External APIs
Make HTTP requests to external APIs. Useful for testing external communication and tracing in Application Insights.
- Current request viewer
Azure App Services
- File System
Explore the local file system. - Local Cache
Explore the App Services local cache feature.
- File System
Azure Storage tools
- Blob Storage Tools
Read and create blobs. - Create a user delegation SAS token
Create a sample token to access a blob in blob storage. - File System Explorer
Explore the local file system. - Redis Explorer
Write and read keys from Redis.
- Cosmos DB
(coming soon)
- Blob Storage Tools
Azure Events and Messaging
- Event Grid
Send events to Event Grid
- Event Hubs
Produce and consume Event Hub events - WebHooks
Receive webhook requests from EventGrid and other services.
- Event Grid
- Azure Identity Tools
- DefaultAzureCredentials
Explore the inner workings of this TokenCredential. - Token caching
Explore how the token caching varies across the different Token Credentials. - Token Credentials Explorer
Explore the different Token Credentials. - Azure.Identity event log viewer
Explore and view the internal event log.
- DefaultAzureCredentials
- Diagnostics and system information
- Runtime Details
Show details about the current runtime and operating system. - Environment Variables
View all the environment variables. - Errors
Trigger different error pages. - Network Details
Show details about the network interfaces. - Scale-out and load balancing
Visualize the effects of load-balancing
- Runtime Details
- Azure Logging
- Logging
Write a message to the standard log - Log Analytics Workspace
Write messages to this service.
- Logging
- Other tools
- Caching and CDN
Explore the effect of caching and CDN.
- Health checks
- Caching and CDN
More tools will be added over time. If you have suggestions, feel free to contact the author, submit an issue, or contribute via a pull request.
Deploying Cloud Debugger for Azure
The Cloud Debugger is also designed to be highly flexible in its deployment options. The same service can be deployed across multiple environments using the provided PowerShell scripts, which makes it versatile for various use cases. It supports the following target environments:
- Azure App Services
- Windows
- Linux
- Linux Containers
- Azure Container Instances
- Azure Container Apps
This allows the service to be deployed across multiple environments, enabling comparisons of application behavior in each. One PowerShell script, BuildAndDeployAll.ps1, will build and deploy to all five environments in one operation.
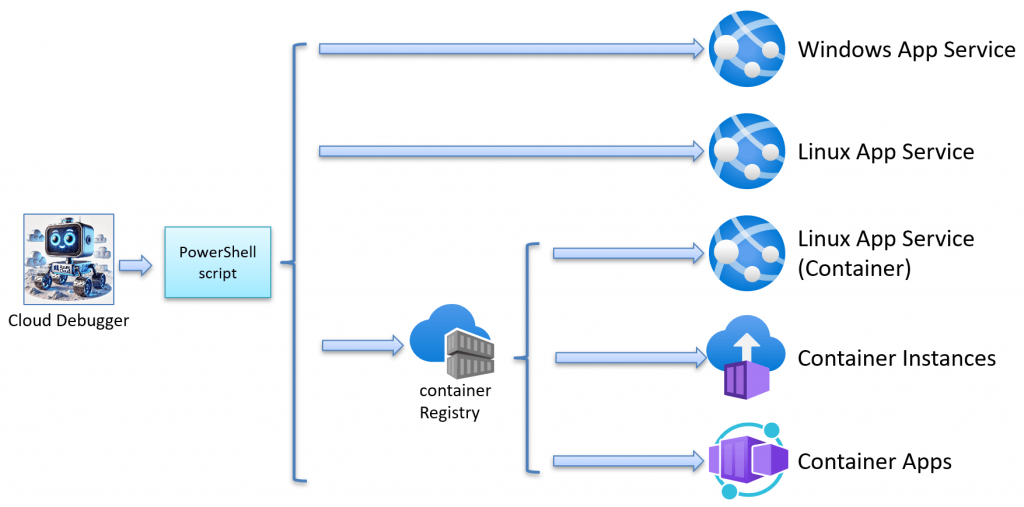
Equally important is the DeleteAllResources.ps1 script, which will delete the Cloud Debugger resource group and its content. I typically run this script at the end of the day to save money and resources.
Why are we using PowerShell to deploy?
Mastering Azure CLI was essential for the AZ-204 certification, and using PowerShell provided hands-on experience with low-level deployment. This approach prepares me to transition to higher-level tools like Azure Bicep, which I plan to explore by converting these scripts in the future.
Cloud Debugger Implementation Details
The Debugger is implemented as a standard ASP.NET Core 8 application written in C#.
Continious Integration
A GitHub Action is triggered with every commit to automatically verify that the project builds correctly. However, we currently handle deployment to Azure using local PowerShell scripts, rather than deploying directly from GitHub.
Customized ASP.NET Core Libraries
We pulled down the source code for Azure.Identity and HttpLogging then converted them into custom class libraries to get better insights and integration with this tools. We also tweaked the namespaces of these two libraries to avoid naming collisions.
- Azure.Identity
We patched this library to gain better insight into how the different Token Credentials behave internally. You can see this when you use the various Identity tools there. - Microsoft.AspNetCore.HttpLogging
This ASP.NET Core class library has been patched to improve the logging of incoming requests to the application, providing better insights into request details.
Secure Development Practices
We try to follow secure development practices, using tools that run with each pull request to prevent bugs, code smells, and security vulnerabilities from entering the cloud environment.
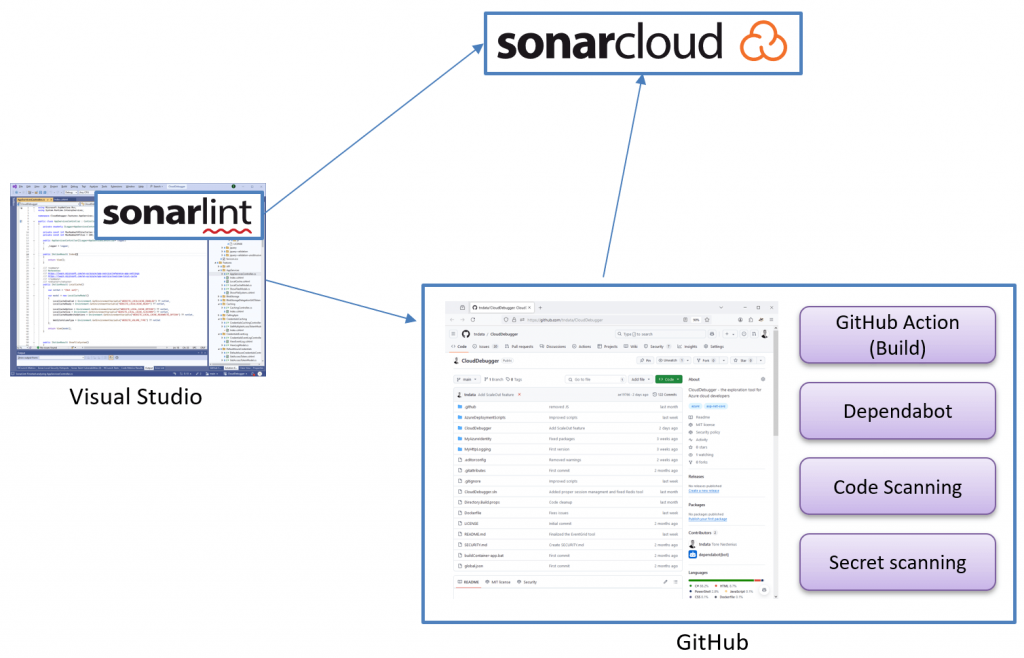
The tools we use are:
- SonarCloud
Provides cloud-based static code analysis to detect code quality issues and vulnerabilities. - SonarLint
A lightweight IDE extension that helps catch code issues in real-time during development. - GitHub Dependabot.
Automatically updates dependencies to help you avoid security vulnerabilities and outdated libraries. - GitHub Code Scanning
Identifies potential security issues and bugs in the code by scanning the repository. - GitHub Secrets Scanning
Detects exposed secrets and sensitive data in the repository to prevent leaks and security breaches.
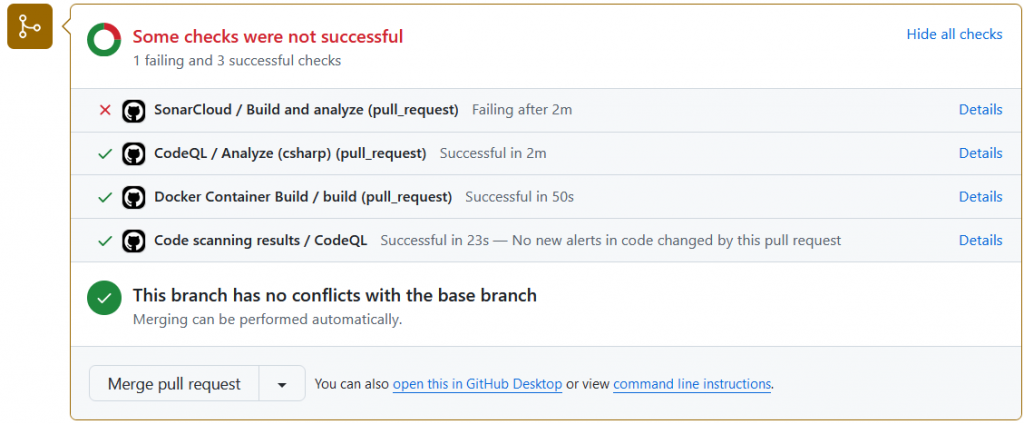
Here is what it can look like when a pull request does not pass all the checks:
Important Azure Security Consideration
It is important not to run this tool in your production environment because it can expose internal secrets, keys, access tokens, and other sensitive information. The tool can also create or send content to various Azure services, which could lead to unintended changes or security risks if it is misused.

Crucially, you must lock down this tool to ensure that only authorized users can access it. Currently, the tool does not provide any built-in feature to restrict access, so additional security measures must be implemented separately.
Getting Started with the Cloud Debugger for Azure
The tool is now available on GitHub; you can start using it by following the deployment guide.
The extensive documentation offers everything you need to get up and running quickly, focusing on providing the shortest path to value.
Join Us, Feedback and Contribute to the project
Cloud Debugger is open source, and we welcome contributions! Whether you’re interested in adding new features, fixing bugs, or sharing your experiences with us and the community, we’d love to hear from you. Check out our GitHub repository and join our growing community there.
About the author
Hi, I’m Tore! I have been fascinated by computers since I unpacked my first Commodore VIC-20. Today, I enjoy providing freelance development and developer training services, focusing on ASP.NET Core, IdentityServer, OpenID Connect, Architecture, and Web Security. You can connect with me on LinkedIn and Twitter, and you can find out more about me and my services here, as well as my courses for developers, including my course, Introduction to IdentityServer and OpenID-Connect.
Other Blog Posts by Me
Tore’s Newsletter
Be the First to Know! Get notified about my latest blog posts, upcoming presentations, webinars, and more — subscribe today!